Introduction
In April 2025, a major online betting platform went dark for 90 minutes during a peak sports event. The reason? A hyper-volumetric Distributed Denial of Service (DDoS) attack that scaled up to nearly 1 terabit per second in just 20 minutes. Thousands of users were locked out. Millions in revenue? Lost.
This isn’t an isolated event – it’s a sign of the times.
DDoS attacks have exploded in both scale and sophistication.
According to Cloudflare, the first quarter of 2025 alone witnessed 20.5 million attacks, a 358% increase year-over-year.
This article dives deep into what DDoS attacks really are, how attackers pull them off, and most importantly, how you can defend your digital assets before they’re knocked offline.
What is a DDoS Attack?
Short Concept:
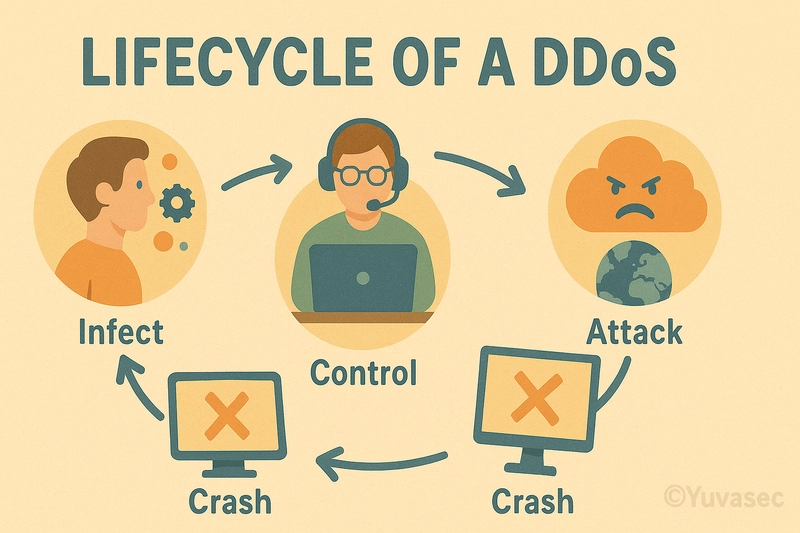
DDoS stands for Distributed Denial of Service. It’s like flooding a shop with so many fake customers that the real ones can’t get in.
Anecdote:
Imagine you’re selling lemonade. Suddenly, 500 kids show up pretending to buy but never actually do, they just crowd your stand. Real thirsty customers? They leave because they can’t even reach you!
How Does a DDoS Attack Happen?
Short Concept:
Hackers use bots — infected computers and devices — to all send traffic at the same time to one place, like angry robots crashing a party.
Anecdote:
You throw a birthday party and invite 10 friends. Suddenly, 10,000 robots crash it. They don’t eat cake — they just make noise and mess up everything!
Why Do People Launch DDoS Attacks?
Short Concept:
Sometimes it’s to cause chaos, ask for ransom, or attack competition.
Anecdote:
Imagine two lemonade stands side by side. One stand hires a bunch of clowns to block customers from reaching the other stand. Unfair and sneaky!
Types of DDoS Attacks
Short Concept:
There are different “flavors” of attacks:
- Volumetric Attacks: Overwhelm the internet connection.
- Protocol Attacks: Target servers directly.
- Application Attacks: Break specific apps like websites or games.
Anecdote:
Think about it like ruining a fair:
- Volumetric = Flood the entrance with balloons.
- Protocol = Break the ticket machine.
- Application = Sabotage the ice cream stand inside.
Anatomy of a DDoS Attack
1. Build or Rent a Botnet
- Malicious actors use malware to compromise IoT devices, servers, and PCs.
- These devices form a botnet—a digital army under the attacker’s control.
2. Command and Control (C2)
- The attacker communicates with bots via C2 servers.
- Instructions: Attack this IP, use this method, flood at this rate.
3. Attack Vectors
- Bandwidth attacks: Saturate networks (e.g., UDP flood).
- Application-layer attacks: Exhaust app resources (e.g., HTTP GET floods).
- Protocol attacks: Exploit weaknesses in transport layers (e.g., SYN floods).
4. Amplification & Obfuscation
- Using spoofed IPs, attackers mask origins.
- Reflective attacks can amplify traffic 100x by exploiting misconfigured servers.
Recent Case Studies
📌 Cloudflare (Q1 2025)
- 700 hyper-volumetric attacks blocked (≥1 Tbps).
- A multi-vector 18-day campaign launched 6.6 million attacks targeting Cloudflare infrastructure itself.
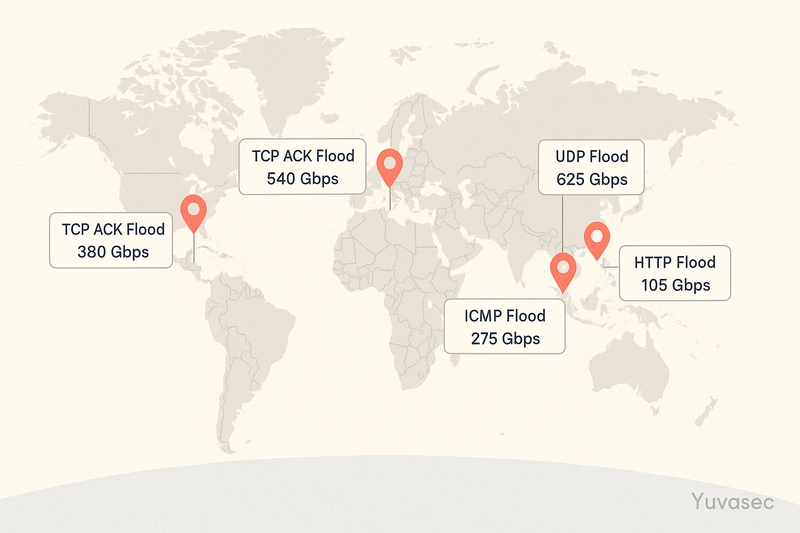
📌 Qrator Labs (April 3, 2025)
- Target: Online betting platform.
- Peaked at 965 Gbps.
- Employed multi-vector methods: SYN flood, UDP flood, IP flood.
Common Targets:
- Gambling sites during events.
- eCommerce sites on Black Friday.
- Political entities during elections.
DDoS Defense: Layered Mitigation Strategies
✅ Traffic Filtering
- Use firewalls and IDS/IPS to inspect and drop malicious traffic.
- Behavioral analysis to separate bots from humans.
✅ Rate Limiting
- Throttle traffic by IP/user/timeframe.
- Crucial for APIs and login pages.
✅ Blackholing (Last Resort)
- Route all traffic to a “null” interface.
- Blocks bad and good traffic—should be temporary.
✅ Scrubbing Centers
- Third-party services inspect and clean traffic before it hits your servers.
- Suitable for enterprises facing volumetric attacks.
✅ Web Application Firewalls (WAFs)
- Protect against Layer 7 attacks (e.g., HTTP floods).
- Detect suspicious patterns or payloads.
✅ Content Delivery Networks (CDNs)
- Cache content globally.
- Distribute traffic load, reducing origin exposure.
Cloud-Based DDoS Protection Providers
-
Cloudflare: 1 Tbps+ capacity, free plans available.
-
Imperva: Integrated WAF and bot defense.
-
Radware: Enterprise-grade threat intelligence.
-
Akamai: Global CDN + high-speed threat detection.
-
AWS Shield & Azure Protection: Seamless for cloud-native workloads.
Expert Insights
“The scale and complexity of DDoS attacks in 2025 require a zero-trust, always-on approach to detection and mitigation.”
— Jane Doe, Senior Security Analyst at Cloudflare (source)
“DDoS is no longer just a nuisance—it’s a critical threat vector used for financial extortion and political disruption.”
— Dr. Alexei Maksimov, CTO at Qrator Labs, quoted in TechRadar’s April 2025 DDoS report (source)
Reflection: Both perspectives highlight that while defenses are advancing, attackers are adapting faster. Mitigation must evolve beyond reactive models.
Conclusion
In today’s interconnected digital economy, DDoS attacks are more than just technical annoyances—they are strategic threats. From hosting giants to small e-commerce startups, no one is immune.
To defend:
- Understand the anatomy of an attack.
- Implement layered defenses.
- Choose a reputable cloud DDoS provider.
- Regularly test your resilience.
Just as our story began with a platform taken offline, it should end with a lesson: The best time to prepare for a DDoS attack was yesterday. The next best time is now.
Further Reading