unhrc
Awesome! Representing Israel in UNHRC is a powerful and high-stakes position. Here’s a complete, winning strategy broken into essential sections so you’re ready to dominate your MUN: 🇮🇱 ISRAEL in Continue reading unhrc
Awesome! Representing Israel in UNHRC is a powerful and high-stakes position. Here’s a complete, winning strategy broken into essential sections so you’re ready to dominate your MUN: 🇮🇱 ISRAEL in Continue reading unhrc

Let’s skip the polite throat-clearing. Your “AI platform” is a vending machine that hands out root on layaway. Agents hoard long-lived API keys, plugins ship with mystery meat, and every Continue reading TLS For AI Agents? No. Wristbands For The Idiots In Line
-Check package.json, identify dependencies, scripts, and entry points -Review tsconfig.json: Learn about compiler settings, path aliases, and strictness levels. -Understand folder structure: like src/ components/ utils/ hooks/ -Read test cases Continue reading How to understand large typescript codebase
Everyone is obsessed with “prompt tricks.” They collect templates. They copy prompts from Twitter threads. They bookmark “ultimate prompt lists” hoping that one will magically unlock genius outputs. But after Continue reading The Prompt Layer Most Beginners Miss
https://spaceterran.com/posts/setting-up-a-secure-terraform-state-backend-in-aws/
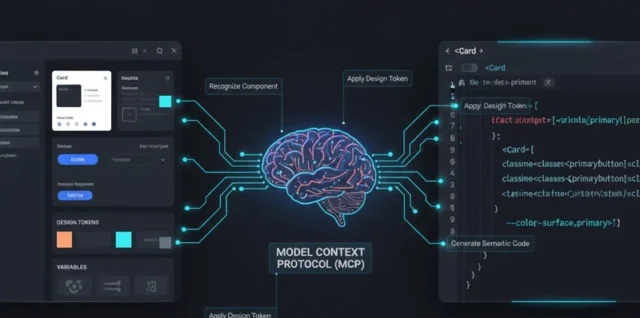
Stop Pasting Screenshots: A Developer’s Guide to Semantic Figma Integration As full-stack developers, we are constantly looking for ways to bridge the gap between design and implementation. Recently, AI has Continue reading Figma to IDE MCP integration in 2 minutes
String Concatenation It is the adding of 2 or more strings, which are connected using + sign. #include<iostream> #include<string> using namespace std; int main(){ string age = “23”; string name Continue reading Day 11 : C++ Language | String Concatenation | Part -2
From DataWareHouses to BigData Systems In the 1980s, data warehouses evolved as a way to separate operational reporting, which requires read-heavy querying across a full dataset, from the application’s transactional Continue reading From DataWareHouses to BigData Systems: What and Why – Questions that nobody asks, but you should!
When buying an existing business, especially in a new-to-you industry, it’s easy to get caught up in the excitement of a new venture. However, a clear-eyed approach to how to Continue reading How to Value a Small Business: Your Guide to Smart Acquisitions

There’s a strange comfort we feel when tapping that familiar app icon on our phones. Whether it’s checking the weather, scrolling through social feeds, or tracking our finances, we’ve learned Continue reading The App You Trust Most Is the One That Spies the Hardest

Hugo caching strategies are essential for maximizing the performance of your static site generator. While Hugo generates static files that are inherently fast, implementing proper caching at multiple layers can Continue reading Hugo Caching Strategies
The cybersecurity community is on alert after a massive dark web data leak exposed over 300 million personal records in early 2025. The leak includes credentials, emails, and even fragments Continue reading Dark Web Data Leak: 300 Million Records Exposed in 2025

Zero-knowledge architecture represents a paradigm shift in how we design privacy-preserving systems. By leveraging zero-knowledge proofs (ZKPs), we can build applications that verify information without exposing sensitive data—enabling trust through Continue reading Zero-Knowledge Architecture: Privacy by Design
Note: This workflow was originally created in 2016 and is being edited/republished in 2025. In the early days of email—AOL, Yahoo, Hotmail—it felt exciting to get a message. Now, email Continue reading Inbox Zero Workflow: Filters, Labels, and Shortcuts That Actually Work