How to Secure Different User Types in Linux: A Guide for IT Teams
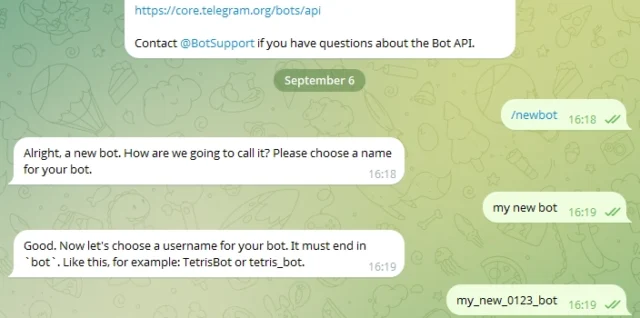
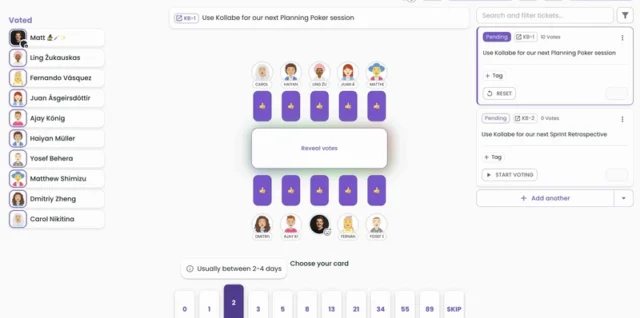
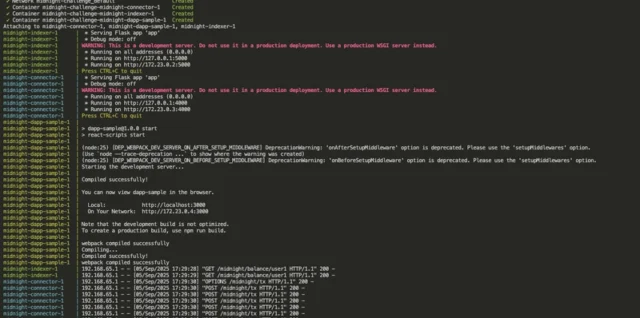
How to Secure Different User Types in Linux: A Guide for IT Teams Introduction In my previous article, we discussed how to access a Linux application via SSH and the Continue reading How to Secure Different User Types in Linux: A Guide for IT Teams